How ProcureChain is using distributed verification to solve the KES 200 billion procurement fraud problem affecting Kenyan businesses
The Procurement Fraud Crisis Nobody Talks About
Every day, somewhere in Nairobi, a procurement manager discovers they’ve been defrauded. The scenario plays out with painful consistency: payment was released three months ago for 1,000 units of raw materials, the delivery note was signed, the invoice matched the purchase order, and the warehouse manager confirmed receipt. But during a routine physical audit, the truth emerges—only 750 units actually arrived. The missing 250 units never existed. The warehouse manager and supplier colluded, split the proceeds from the phantom inventory, and by the time the fraud is discovered, both the money and the culprits have vanished.
This isn’t an isolated incident. This is the daily reality of corporate procurement in Kenya. Conservative estimates suggest Kenyan businesses lose over KES 200 billion annually to procurement fraud, with global losses exceeding $3 trillion. The construction sector sees inflated material costs and phantom deliveries. Manufacturing companies receive substandard raw materials disguised as premium grades. Retail chains discover systematic short-deliveries from distributors. Hospitality groups pay for food and beverage deliveries that arrive partial or adulterated. The problem is so endemic that many companies simply factor a “10-15% shrinkage allowance” into their procurement budgets—essentially budgeting for theft.
The root cause isn’t incompetence or lack of technology. Modern enterprises run sophisticated ERP systems like SAP, Oracle, and Odoo. They’ve implemented approval workflows, purchase order matching, and three-way reconciliation processes. Some have even adopted blockchain solutions promising transparency and immutability. Yet the fraud continues unabated because these systems all share a fundamental architectural flaw: they assume that verification by a single individual is trustworthy.
When your warehouse manager is the sole person confirming that 1,000 units arrived, you’ve created a single point of failure. One person to bribe. One signature to forge. One conscience to compromise. The ERP system dutifully records “1,000 units received” because that’s what the warehouse manager entered. The blockchain creates an immutable record of that entry, but immutability doesn’t equal truth—it just means the lie is permanent. The audit happens weeks or months later, by which time the evidence has disappeared, the supplier has moved on, and recovering the funds is nearly impossible.
Why Blockchain Alone Doesn’t Solve Procurement Fraud
The blockchain and procurement industry has spent the last five years promising revolution. Projects like IBM Food Trust, VeChain, and various academic pilots in Kenya and across Africa have demonstrated that you can put procurement data on a blockchain. Supply chain visibility improves. Data becomes tamper-proof. Transparency increases. These are genuine benefits, but they don’t address the core vulnerability: garbage in, garbage out.
If a corrupt warehouse manager manually enters “1,000 units delivered” into a blockchain system when only 750 arrived, the blockchain faithfully records the false data. The immutability that makes blockchain powerful for audit trails also makes it dangerous for recording lies. Traditional blockchain consensus mechanisms like Proof of Work (Bitcoin) or Proof of Stake (Ethereum) were designed to prevent double-spending of digital currency, not to verify the truth of physical world events. They answer the question “did this transaction occur?” not “did this delivery actually happen as reported?”
Existing enterprise blockchain solutions require trusted data oracles—designated individuals or organizations responsible for inputting accurate data. But this just moves the trust problem around rather than solving it. Instead of trusting the warehouse manager, you’re trusting whoever has oracle privileges. The single point of failure remains, just wearing a different label.
ProcureChain: Multi-Party Verification Consensus for Real-World Procurement
This is where ProcureChain diverges from everything that’s been tried before in blockchain procurement systems. Instead of assuming any single verifier is trustworthy, we require multiple independent parties to confirm delivery details before payment is released. Not as a manual process requiring committee meetings and email chains, but as an automated consensus mechanism built into the procurement workflow itself.
The concept isn’t revolutionary—it’s simply the rigorous application of a principle that should have been obvious all along. When something valuable is at stake, you don’t trust one person’s word. You get multiple independent confirmations. Law requires two witnesses. Science demands reproducible results. Financial audits involve third-party verification. Yet somehow, corporate procurement has been operating on the honor system, trusting individual employees to honestly report million-shilling transactions.
ProcureChain implements what I call distributed verification consensus. When a supplier claims to have delivered 1,000 bags of cement worth KES 2.5 million, our system doesn’t ask one person to verify it. Instead, it automatically requests confirmation from multiple independent sources, each with different incentives, access points, and verification methods. The warehouse officer reports what was physically received. The quality inspector assesses grade and specifications. A finance officer conducts a spot count. GPS and weight sensor data from the delivery truck provides objective measurements. Each verifier submits their assessment independently, without knowing what the others reported.
Then comes the mathematics. This is where ProcureChain stops being just another blockchain procurement platform and becomes something genuinely novel. It does not use simple majority voting where three out of four verifiers agreeing equals approval. That’s too crude. Real-world data has natural variance—one verifier might count 998 units, another 1,002, a third 1,000 exactly. These small discrepancies are normal and don’t indicate fraud. But when one verifier reports 1,000 units while three others report 750, that’s a red flag screaming for attention.
The consensus algorithm treats each verification as a data point in phase space, characterized by the verifier’s historical accuracy (their reputation score), their response speed (how quickly they submitted), the content of their report, and their consistency patterns over time. Then, perform what’s essentially an interference analysis across all submitted verifications. When verifiers are reporting similar values, their data “resonates” constructively, producing high confidence scores. When one verifier’s report conflicts sharply with the others, it creates destructive interference, flagging that specific verifier as a potential outlier.
The output isn’t binary. We (all of us who use it) don’t just say “approved” or “rejected.” Instead, every transaction receives a confidence score from 0-100%. A score of 94% might mean all four verifiers reported values within 2% of each other, their historical accuracy is high, and objective sensor data aligns with subjective human reports—high confidence, approve payment immediately.
– A score of 58% might indicate moderate disagreement between verifiers or one verifier with a concerning track record—caution warranted, additional verification recommended. – A score of 23% flags severe discrepancies and automatically identifies which specific verifier is the outlier—block payment, investigate immediately.
This is pre-emptive fraud detection. The fraudulent warehouse manager who reports 1,000 units when only 750 arrived gets caught before the payment is released, not six months later during an audit. The system automatically alerts management that Verifier #3’s report conflicts with all other data sources, providing a confidence score for the fraud likelihood. No money leaves the company. No elaborate recovery process is needed. The fraud is stopped at the point of origin.
The Four-Layer Verification Architecture
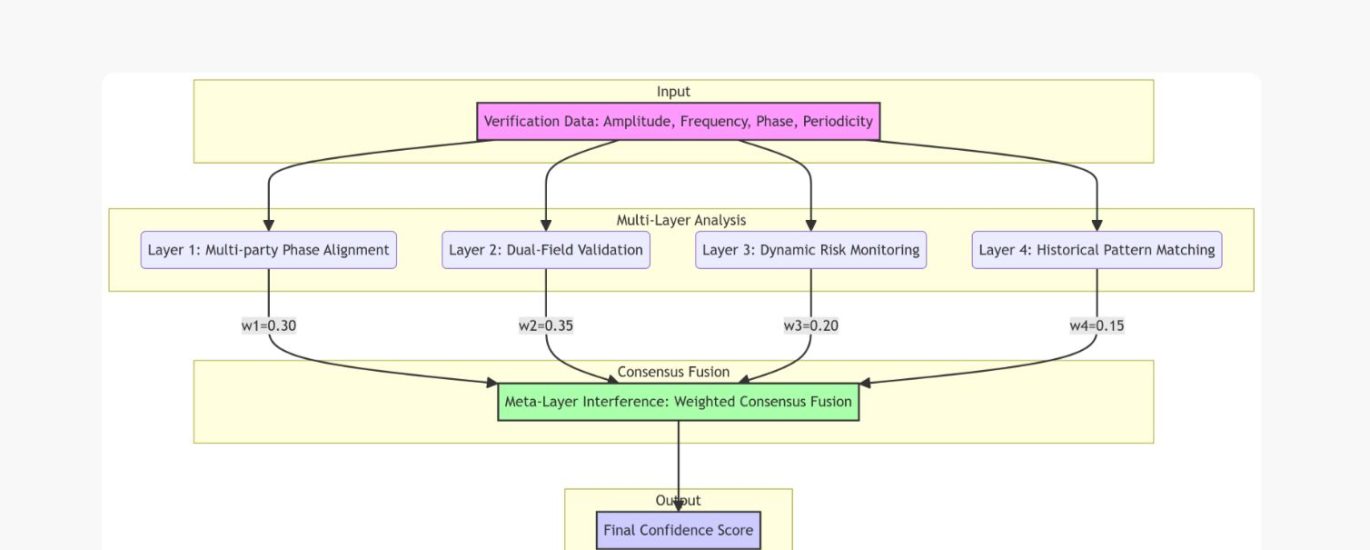
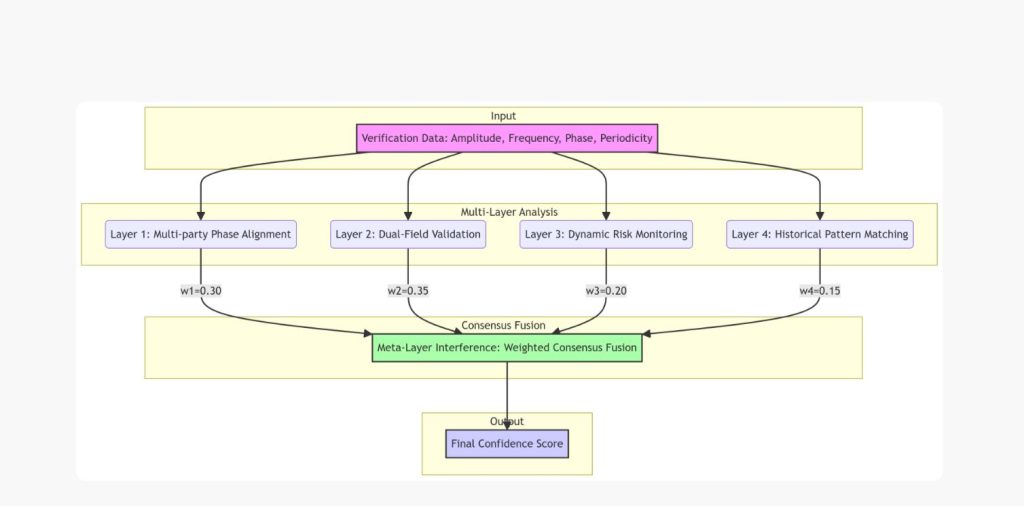
ProcureChain doesn’t rely on just one type of analysis. The system runs four parallel verification layers, each examining the transaction from a different angle, then combines their outputs through weighted meta-analysis to produce the final confidence score and recommendation.
Layer One: Multi-Party Phase Alignment
This layer examines how well the different verifiers agree with each other. We require a minimum of four independent verifiers for any transaction—this isn’t arbitrary, it’s based on geometric principles ensuring no two verifiers can collude to override the consensus without detection. The system calculates pairwise agreement between all verifier pairs, looking for patterns. If Verifiers A, B, and C all report similar values but Verifier D is an outlier, the math identifies D as the problem. If all four verifiers are reporting wildly different numbers, it signals either a genuinely ambiguous situation or a more complex fraud involving multiple parties. The confidence score reflects this alignment, with tightly clustered reports producing high scores and scattered reports triggering caution or blocking.
Layer Two: Objective versus Subjective Field Validation
This layer distinguishes between objective sensor data and subjective human reports. Objective data comes from calibrated IoT devices: weight scales with ±0.1% accuracy, GPS trackers providing location and timing data, temperature sensors for cold chain verification, automated timestamp servers. Subjective data comes from human observers: delivery notes, quality assessments, visual inspections, satisfaction ratings. The system compares these two data fields and looks for discrepancies. If the truck’s weight sensor indicates 750 bags but the human warehouse manager reports 1,000, that’s destructive interference between objective and subjective fields—a strong fraud indicator. If both fields align, it’s constructive interference, dramatically increasing confidence. This dual-field approach catches a category of fraud that pure human or pure automated systems miss.
Layer Three: Adaptive Risk-Based Monitoring
Not all suppliers and not all transactions carry equal risk. A supplier with ten years of perfect delivery history and clean regulatory status doesn’t need the same scrutiny as a new supplier with tax compliance issues and a history of late deliveries. This layer continuously monitors risk indicators from external data sources: Kenya Revenue Authority tax compliance APIs, credit bureau reports, regulatory authority databases, historical performance metrics. Based on this multi-source risk assessment, the system dynamically adjusts validation frequency and payment terms. Low-risk suppliers might get monthly spot checks with net-30 payment terms. High-risk suppliers face weekly verification requirements with payment-on-delivery-only terms. Critical-risk suppliers trigger daily monitoring and payment blocking until issues are resolved. The thresholds adapt in real-time as new information arrives, creating a responsive rather than static risk management system.
Layer Four: Historical Pattern Matching
Every successful procurement transaction creates a data signature: how many verifiers participated, how quickly they responded, what their agreement patterns looked like, whether any issues arose, what the final outcome was. The system stores these patterns on-chain and uses them for predictive analysis on future transactions. When evaluating a new procurement, the system searches for similar historical patterns: same industry, similar order value, comparable supplier characteristics, matching time frames. If current transaction data resonates strongly with past successful patterns, confidence increases. If it matches patterns that historically preceded fraud or disputes, warning flags appear. This creates institutional memory that improves over time—the system literally learns from experience, becoming more accurate with every transaction processed.
Meta-Layer: Weighted Interference Fusion
The four layers don’t operate in isolation. The final consensus emerges from weighted combination of all four analyses. Objective sensor data (Layer Two) carries the highest weight at 35% because physics doesn’t lie—if the scale says 750 bags, it’s 750 bags. Multi-party alignment (Layer One) weighs 30% because independent verification is the foundation of the whole system. Risk-based pressure (Layer Three) contributes 20% because context matters—the same discrepancy means different things for different suppliers. Historical patterns (Layer Four) add the final 15% as guidance rather than deterministic input. The weighted average produces the final confidence score, decision recommendation, and if applicable, identification of which specific verifier appears fraudulent.
Blockchain Procurement Implementation in Kenya: Technical Architecture
ProcureChain runs on a permissioned blockchain infrastructure optimized for enterprise procurement workflows in the Kenyan market. Why? For several pragmatic reasons: transaction speed requirements (procurement decisions need seconds, not minutes), privacy concerns (companies don’t want competitors seeing their procurement data), and regulatory compliance (Kenya’s data protection laws require controlled access).
The technical stack consists of several integrated components working in concert. The blockchain layer provides immutable storage (considering and needs more storage capacity) for all verification data, confidence scores, and payment decisions—this creates the audit trail that satisfies compliance requirements and provides evidence in case of disputes. The consensus engine implements the mathematical algorithms for phase-space analysis, interference detection, and confidence scoring—this is where the novel intellectual property lives. The API gateway handles integration with external systems. The notification system ensures all relevant stakeholders receive real-time alerts when verification is needed or when anomalies are detected. The analytics dashboard gives procurement managers visibility into trends, patterns, and risk indicators across all their transactions.
For companies adopting ProcureChain, the integration pathway is designed to be gradual rather than disruptive. I am not asking businesses to rip out their existing ERP systems and replace everything with blockchain. Instead, ProcureChain operates as a verification layer that sits alongside current procurement systems.
In the simplest deployment, companies can use our standalone web dashboard with zero integration—procurement managers manually log into ProcureChain when they need multi-party verification for a high-value or high-risk transaction. This proves value immediately without requiring IT department involvement or months-long integration projects.
As the system proves its worth, it moves toward API integration. When a purchase order reaches the delivery stage in their existing ERP system, the ERP sends a webhook to ProcureChain triggering the verification workflow. The system handles the entire verification process, coordinates with the multiple verifiers, performs the consensus analysis, and sends back a simple approve/reject/investigate recommendation. Currently looking at how the ERP can then conditionally release payment based on the response. This lightweight integration provides automation while maintaining separation of concerns—their ERP handles procurement, we handle verification.
For enterprises requiring deeper integration, fear not, looking at common ERP platforms in the Kenyan market.
Blockchain Tendering and Procurement: The Kenyan Market Context
Kenya’s procurement landscape is undergoing rapid digital transformation. The government’s push toward e-procurement through systems like IFMIS and e-GP have created awareness and readiness for digital procurement solutions. Private sector companies are increasingly seeking alternatives to manual, paper-based procurement processes that are slow, opaque, and vulnerable to manipulation. However, the market is sophisticated enough to be skeptical of “blockchain for blockchain’s sake” projects that add complexity without solving real problems.
This creates both opportunity and challenge for blockchain procurement solutions in Kenya. The opportunity lies in addressing genuine pain points that existing systems don’t solve: procurement fraud, verification bottlenecks, payment disputes, supplier trust issues, and audit trail requirements. The challenge is demonstrating that blockchain adds concrete value beyond what a well-designed centralized database could provide.
ProcureChain’s value proposition for the Kenyan market specifically addresses these considerations. The multi-party verification consensus solves the single-point-of-failure problem that plagues both manual and automated procurement systems. The blockchain’s immutability provides the audit trail that Kenyan companies need for compliance with internal controls, external audits, and increasingly stringent corporate governance requirements. The transparency is selective—participating parties can see relevant verification data for their transactions, but competitors and the public cannot, respecting commercial confidentiality while enabling accountability among authorized stakeholders.
The target market isn’t government procurement initially, despite government spending representing a larger total addressable market. Government procurement in Kenya operates under specific regulatory frameworks, involves political considerations, and has long sales cycles requiring extensive stakeholder management.
Instead, ProcureChain is focusing on private sector companies with clear procurement pain points and faster decision-making processes. Start-ups, SMEs, Manufacturing companies losing money to substandard raw materials. Retail chains dealing with systematic short-deliveries. Construction firms managing complex supply chains for multiple simultaneous projects. Hospitality groups requiring quality and cold chain verification for food and beverage deliveries.
These companies share common characteristics that make them ideal early adopters: they’re already digitizing their operations, they have procurement budgets large enough that fraud losses are material, their procurement managers have decision-making authority without requiring months of committee approvals, and they’re motivated to solve the problem because it’s costing them money right now. A mid-market manufacturing company spending KES 10 million annually on procurement and experiencing 10% fraud losses is losing KES 1 million per year—our subscription cost is a fraction of that, making ROI obvious and immediate.
Why This Approach Could Actually Work
Procurement blockchain projects have been announced with great fanfare for years, yet most remain pilots that never scale or academic papers that never commercialize. The graveyard of failed blockchain procurement initiatives is vast: supply chain tracking systems that required too much manual data entry, verification platforms that couldn’t integrate with existing systems, solutions that were technologically impressive but commercially impractical. Why should ProcureChain be different?
First, its solving a specific, expensive problem rather than pursuing blockchain for its own sake. Procurement fraud costs Kenyan businesses real money. Every prevented fraud generates quantifiable ROI. The value proposition isn’t “you’ll have immutable records” (nice to have) but rather “you’ll stop losing millions to procurement fraud” (urgent need).
Second, the technical innovation is defensible. While keeping the details of the consensus algorithm confidential, the approach of applying circular statistics and phase-space analysis to multi-party verification is novel. It’s not just “put procurement data on blockchain” which anyone can do. It’s a specific method for calculating confidence scores and identifying fraudulent verifiers that produces better results than simple majority voting or trusted oracle models.
Third, ProcureChain is designed for gradual adoption rather than requiring a forklift upgrade. Companies can start using ProcureChain tomorrow with their existing systems, manually at first, then progressively integrating as value is proven. This lowers the adoption barrier dramatically compared to solutions that require replacing entire procurement infrastructure.
Fourth, the timing is right for Kenya specifically. Digital procurement adoption is accelerating, fraud awareness is high, and companies are actively seeking solutions. We’re not trying to create the market—the market exists and is growing. ProcureChain is just offering a better answer to a problem companies already know they have.
Fifth, network effects create defensibility over time. Every transaction processed improves the system’s pattern recognition. Every verified supplier builds reputation capital that transfers across customers. As more companies join, the network becomes more valuable to participants, creating switching costs and competitive moats that go beyond just the technology.
Where ProcureChain is and What Comes Next
ProcureChain exists today as a working proof-of-concept. The core consensus algorithm is functional and the blockchain infrastructure is operational. The basic web dashboard allows verification workflow management. What ProcureChain does not have yet is production deployments with real companies processing actual procurement transactions.
That’s the stage ProcureChain is at: technically validated, commercially unproven. The technology works in controlled conditions. Whether it works in the chaos of real-world corporate procurement remains to be demonstrated. This is why I am looking for design partner customers—companies willing to test ProcureChain with genuine transactions, not pilots with fake data. These early customers will shape the product through their feedback, identify gaps between theory and practice, and help me understand which features matter most versus which are nice-to-have.
For companies considering becoming design partners, the value proposition is straightforward: heavily discounted lifetime pricing locked in perpetually, direct influence over product development roadmap, early access to all new features, and most importantly, a solution to a problem that’s currently costing you money. The risk is that you’re adopting early-stage technology that will have bugs, missing features, and require patience. The reward is that you help build the solution you actually need rather than accepting whatever vendors think you want.
For those wondering about the business model and sustainability, I am building ProcureChain as a SaaS platform with revenue generated through per-transaction fees or monthly subscription tiers depending on customer preference and transaction volume. ProcureChain is not venture-backed unicorn chasers demanding hockey-stick growth at all costs thus building a sustainable business that solves a real problem for customers willing to pay because the ROI is obvious. If ProcureChain can sign ten customers each processing KES 50 million in annual procurement, preventing even 5% fraud saves them KES 25 million collectively—more than enough to support a reasonable subscription fee and fund continued development.
The immediate development roadmap focuses on three priorities. First, mobile applications for field verifiers that work offline and sync when connectivity is available—because Kenya’s last-mile internet infrastructure isn’t always reliable, and we (all of us) need verification to work regardless. Second, API integration frameworks and pre-built connectors for common ERP systems in the Kenyan market, starting with Odoo—because lowering integration friction accelerates adoption. Third, enhanced analytics and reporting dashboards that surface trends, patterns, and insights from the verification data—because preventing the next fraud is even more valuable than catching the current one.
An Open Invitation
If you’re a procurement manager tired of discovering fraud months after payment was released, tired of trusting individual employees with million-shilling decisions, tired of accepting procurement losses as an inevitable cost of doing business—we should talk. Not in six months when I’ve built everything. Now, while am still figuring this out, when your input can shape what gets built.
If you’re working on blockchain solutions for supply chain, procurement, or verification in Kenya or across Africa and see potential for collaboration or knowledge sharing—reach out. The ecosystem benefits when we share learnings rather than everyone making the same mistakes in isolation.
If you’re a developer interested in working on genuinely novel applications of distributed systems to real-world problems—the codebase is open, contributions are welcome, and there’s plenty of hard technical problems left to solve.
If you’re someone who invests in early-stage technology companies solving expensive problems in emerging markets—ProcureChain not actively fundraising right now, yet, but open to conversations around this project and others as well in the pipeline, and especially with people who understand the problem space and see the opportunities.
If you’re just intellectually curious about how blockchain consensus mechanisms could apply to physical-world verification, or how procurement fraud actually works, or what it takes to build a SaaS platform in Kenya’s B2B market—follow the journey on Linkedin and watch where this goes.
Tenderzville is building ProcureChain because procurement fraud is expensive, preventable, and ubiquitous. Because the solution is technically feasible and commercially viable. Because someone needs to actually implement multi-party verification consensus rather than just writing academic papers about it. And because Kenya’s market is ready for this, right now.
The technology works. The economics make sense. The problem is real. What happens next depends on finding the right early customers willing to validate this in production. If that’s you, let’s talk.
Connect With ProcureChain
For Design Partner Inquiries: Email with “Design Partner” in the subject line. Tell me about your procurement spend, main fraud pain points, and what success would look like for you. First conversations are exploratory with no commitment required.
For Technical Discussions: I am particularly interested in feedback on the consensus algorithm implementation and integration architecture.
For Collaboration or Investment: Reach out directly. I will respond to everyone who takes the time to engage seriously with what Tenderzville is building.
ProcureChain is here-ish!
Its a major milestone. Thank you for reading and engaging.